Smart Contract Deployment: Streamlining Digital Processes
Introduction:
Smart contract deployment has become a cornerstone of blockchain technology, revolutionizing the way digital agreements are executed. This article explores the significance of smart contract deployment, its underlying principles, and the transformative impact it has on automating and securing various processes.
Understanding Smart Contracts:
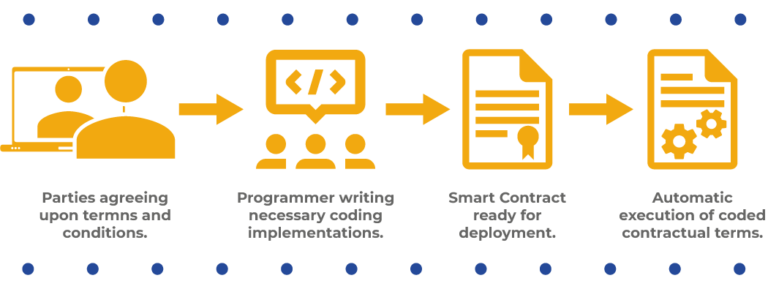
Smart contracts are self-executing agreements with the terms directly written into code. Built on blockchain platforms like Ethereum, these contracts automatically execute and enforce predefined rules when specific conditions are met. Understanding the capabilities of smart contracts is fundamental to appreciating their deployment in diverse use cases.
Coding and Solidity:
Smart contracts are typically written in programming languages, with Solidity being the predominant language for Ethereum-based contracts. Coding smart contracts requires precision and adherence to best practices to ensure their security and functionality. Developers play a crucial role in crafting these digital agreements, translating legal and business logic into code.
Deployment on Blockchain Networks:
Once coded, smart contracts are deployed on blockchain networks. This process involves uploading the contract code to the blockchain, creating a digital representation of the agreement. The decentralized nature of blockchains ensures transparency and immutability, crucial features for the reliability of smart contracts.
Automating Financial Transactions:
One of the primary applications of smart contract deployment is in automating financial transactions. From cryptocurrency transfers to decentralized finance (DeFi) protocols, smart contracts streamline and automate processes that traditionally required intermediaries. This not only reduces the risk of errors but also enhances the speed and efficiency of financial transactions.
Decentralized Applications (DApps):
Smart contracts serve as the backbone for decentralized applications (DApps). These applications, built on blockchain platforms, leverage smart contracts to execute various functions without relying on centralized servers. DApps span industries such as gaming, finance, and supply chain, showcasing the versatility of smart contract deployment.
Tokenization and Initial Coin Offerings (ICOs):
Smart contracts facilitate tokenization, the process of representing assets or securities as digital tokens on the blockchain. Initial Coin Offerings (ICOs) leverage smart contracts to raise funds by distributing tokens to investors. Smart contract deployment in ICOs automates the token distribution process, ensuring transparency and fairness.
Ensuring Security and Auditing:
Security is paramount in smart contract deployment. Flaws in code can lead to vulnerabilities, potentially exploited by malicious actors. Security audits are essential before deploying smart contracts to identify and rectify potential weaknesses. The decentralized and transparent nature of blockchain networks contributes to the overall security of smart contracts.
Oracles for Real-World Data:
While smart contracts operate in a decentralized environment, they often require real-world data to execute conditions. Oracles act as bridges between the blockchain and external data sources. Smart contract deployment involving oracles enables the integration of off-chain information, expanding the scope of applications to real-world scenarios.
Challenges and Evolving Standards:
Despite their advantages, smart contract deployment faces challenges, including code vulnerabilities and the need for evolving standards. Continuous advancements, research, and the establishment of best practices contribute to addressing these challenges. Smart contract developers actively contribute to the evolution of standards for secure and reliable deployment.
Conclusion:
In conclusion, smart contract deployment stands at the forefront of blockchain innovation, offering a decentralized, automated, and secure way to execute digital agreements. From financial transactions to decentralized applications, the versatility of smart contracts is reshaping how we engage in digital processes. As blockchain technology continues to evolve, smart contract deployment will play a pivotal role in shaping the future of decentralized and automated systems.
To explore more about Smart Contract Deployment, visit here. Understanding the intricacies of smart contracts and their deployment is crucial for anyone navigating the dynamic landscape of blockchain technology.