Decoding Consensus Algorithms: A Comparative Analysis
Unraveling the Tapestry: A Comparative Analysis of Consensus Algorithms
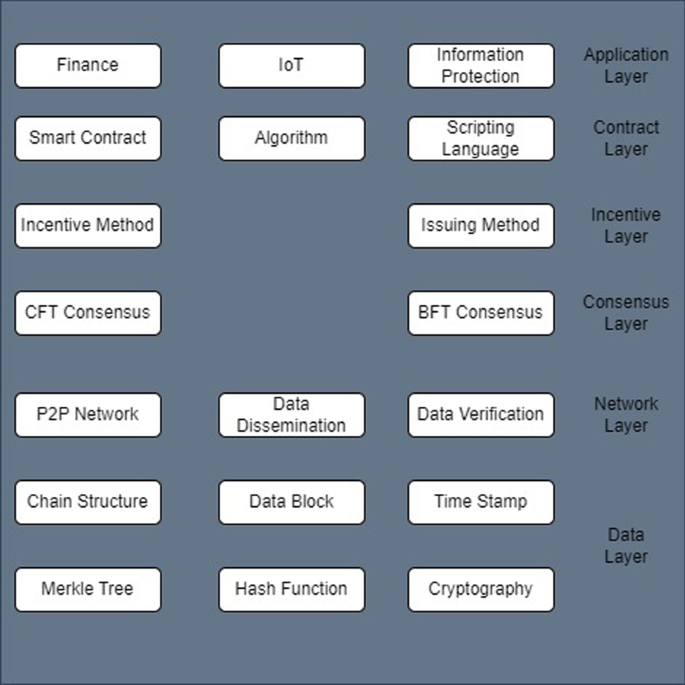
Consensus algorithms lie at the heart of blockchain technology, governing how distributed networks agree on the state of the system. In this exploration, we embark on a journey to compare and contrast various consensus algorithms, shedding light on their strengths, weaknesses, and real-world applications.
Proof-of-Work (PoW): The Pioneer
Proof-of-Work, the original consensus algorithm introduced by Bitcoin, relies on miners solving complex mathematical puzzles to validate transactions and add them to the blockchain. While PoW provides security, its energy-intensive nature has spurred concerns about sustainability and environmental impact. Yet, its resilience remains undeniable, making it a foundational choice for several prominent blockchains.
Proof-of-Stake (PoS): Shifting the Paradigm
In contrast to PoW, Proof-of-Stake assigns the right to validate blocks based on the number of coins a participant holds. This alternative consensus algorithm aims to address the energy concerns associated with PoW. PoS systems often tout faster transaction processing times and reduced environmental impact, making them increasingly popular in the blockchain space.
Delegated Proof-of-Stake (DPoS): Streamlining Decision-Making
DPoS builds upon the PoS model by introducing a select group of delegates responsible for validating transactions. Chosen by the community through voting, these delegates streamline decision-making and enhance network efficiency. DPoS strikes a balance between decentralization and scalability, offering a governance layer to the consensus process.
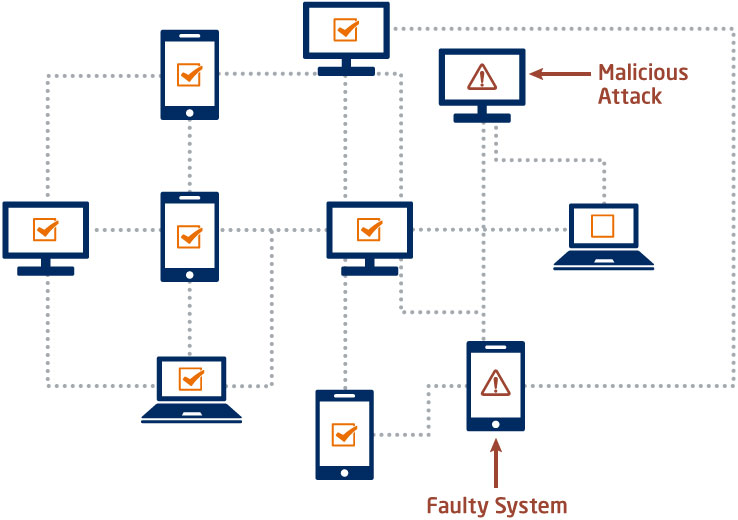
Practical Byzantine Fault Tolerance (PBFT): Swift and Efficient
PBFT is a consensus algorithm designed for permissioned blockchains, focusing on efficiency and speed. Participants, known as nodes, communicate to achieve consensus quickly. PBFT is suitable for scenarios where participants are known and trusted, providing a more streamlined approach to consensus without the need for extensive computational work.
Raft Consensus: Simplifying Distributed Systems
Raft is another consensus algorithm designed for simplicity and ease of understanding. It divides the consensus process into leader election, log replication, and safety mechanisms. Raft’s straightforward design makes it an excellent choice for educational purposes and scenarios where a simplified consensus algorithm is preferred.
Practical Comparison: Navigating Choices
To understand the practical implications of these consensus algorithms, explore Consensus Algorithm Comparison. This platform offers a hands-on comparison of different consensus models, providing insights into their applications and helping users make informed decisions when choosing a consensus algorithm for their blockchain projects.
The Evolution of Consensus: Challenges and Innovations
While these consensus algorithms have their strengths, challenges persist in achieving the perfect balance between security, decentralization, and scalability. Ongoing research and innovations aim to address these challenges, with new consensus models and hybrid approaches emerging to create more resilient and adaptable blockchain networks.
Future Considerations: Beyond the Horizon
As the blockchain space continues to evolve, consensus algorithms will play a pivotal role in shaping the future of decentralized systems. Innovations such as Proof-of-Stake improvements, hybrid models, and consensus customization are likely to influence the next generation of blockchain networks.
Navigating the Diverse Landscape
In conclusion, the world of consensus algorithms is a diverse landscape with each model offering unique advantages and trade-offs. Understanding the nuances of Proof-of-Work, Proof-of-Stake, Delegated Proof-of-Stake, Practical Byzantine Fault Tolerance, and Raft provides a foundation for navigating the complexities of blockchain technology. The journey towards consensus is ongoing, with each algorithm contributing to the rich tapestry of decentralized systems.