Secure Insights: Navigating Blockchain Privacy Technologies
Secure Insights: Navigating Blockchain Privacy Technologies
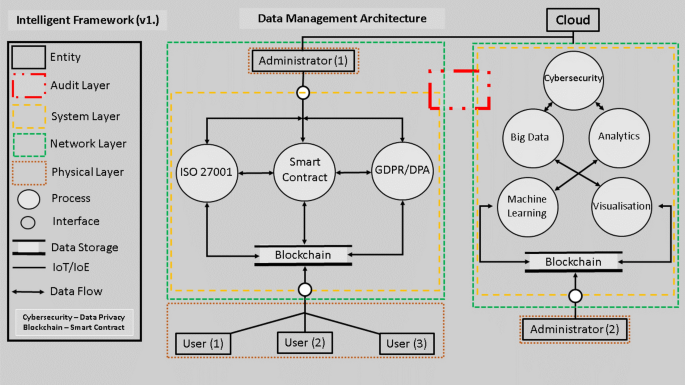
In the realm of blockchain technology, privacy has emerged as a critical concern. Blockchain privacy technologies play a pivotal role in addressing these concerns, offering innovative solutions to safeguard sensitive information while preserving the transparency and immutability inherent to blockchain systems.
The Significance of Privacy in Blockchain: Balancing Transparency and Confidentiality
Blockchain’s foundational principles of transparency and immutability are essential for trust and accountability. However, in certain use cases, preserving user privacy becomes paramount. Blockchain privacy technologies aim to strike a delicate balance between the transparency required for trust and the confidentiality necessary to protect sensitive data.
Zero-Knowledge Proofs: Verifying without Revealing
Zero-knowledge proofs (ZKPs) stand as a cornerstone in blockchain privacy. These cryptographic protocols allow one party to prove the authenticity of information to another without revealing the actual data. ZKPs enable transactions to be verified without disclosing the transaction details, offering a powerful solution for privacy-conscious applications.
Ring Signatures and Confidential Transactions: Anonymizing Blockchain Transactions
Ring signatures and confidential transactions contribute to blockchain privacy by anonymizing transaction details. Ring signatures enable a user to sign a transaction on behalf of a group, concealing the actual signer. Confidential transactions hide the transaction amount, ensuring that financial details remain private while still being verifiable by network nodes.
Homomorphic Encryption: Performing Operations on Encrypted Data
Homomorphic encryption is a revolutionary technology that allows computations to be performed on encrypted data without decrypting it. In the context of blockchain, this ensures that sensitive information remains confidential even during processing. Homomorphic encryption enhances privacy in scenarios where data manipulation is required without compromising security.
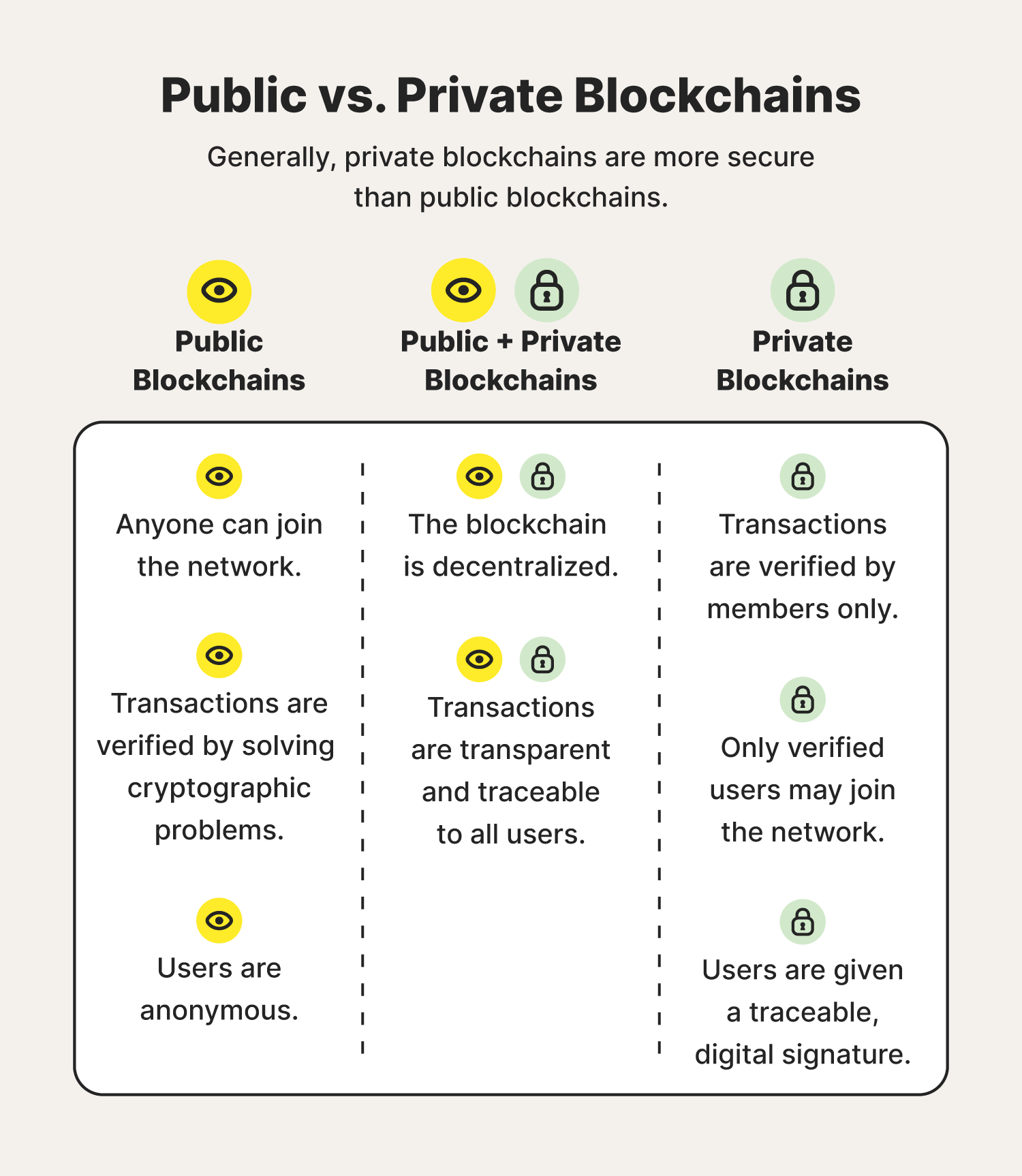
Privacy Coins: Tailoring Transactions for Confidentiality
Privacy-focused cryptocurrencies, often referred to as privacy coins, integrate specialized features to enhance confidentiality. Monero, Zcash, and Dash are examples of privacy coins that utilize advanced cryptographic techniques to obfuscate transaction details, providing users with enhanced privacy options compared to traditional cryptocurrencies.
Sidechains and Off-Chain Solutions: Privacy Beyond the Main Blockchain
Sidechains and off-chain solutions offer additional layers of privacy by conducting certain transactions off the main blockchain. By moving specific activities away from the public ledger, these solutions reduce the visibility of transactions and information, enhancing the overall privacy of blockchain networks.
Decentralized Identity and Self-Sovereign Identity: Empowering Users
Decentralized identity (DID) and self-sovereign identity (SSI) are privacy-centric concepts that empower individuals to control their identity information on the blockchain. Users can selectively share identity attributes without relying on centralized authorities, enhancing privacy and security in digital interactions.
Governance and Privacy: Navigating Regulatory Frameworks
The intersection of governance and privacy in blockchain is crucial, especially in compliance with regulatory frameworks. Privacy-preserving technologies should align with legal requirements, ensuring that blockchain applications adhere to data protection regulations without compromising the fundamental principles of decentralization and user control.
Blockchain Privacy Challenges: Overcoming Hurdles for Mainstream Adoption
Despite the advancements in blockchain privacy technologies, challenges persist. Balancing privacy with regulatory compliance, ensuring scalability, and addressing interoperability issues are among the hurdles that must be overcome for widespread adoption. Collaborative efforts within the blockchain community are essential to navigate these challenges successfully.
The Future of Blockchain Privacy: Innovations and Integration
The future of blockchain privacy is marked by continuous innovations and integrations. As the technology evolves, novel approaches, such as secure multi-party computation and privacy-preserving smart contracts, are being explored. The integration of these advancements into blockchain ecosystems will further enhance privacy and contribute to the mainstream adoption of blockchain technology.
In conclusion, navigating blockchain privacy technologies is a nuanced journey that involves embracing cryptographic innovations, privacy-focused cryptocurrencies, and decentralized identity solutions. As the blockchain landscape continues to evolve, prioritizing user privacy while maintaining the integrity of decentralized networks remains a key focus. To explore more about Blockchain Privacy Technologies, visit fireboyandwatergirlplay.com.