Building Trust: Navigating Byzantine Fault Tolerance Models

Navigating Byzantine Fault Tolerance Models for Trustworthy Systems
In the realm of distributed systems, Byzantine Fault Tolerance (BFT) models stand as guardians against malicious actors and system failures. This article explores the significance, types, and applications of Byzantine Fault Tolerance, shedding light on their role in building trustworthy and resilient systems.
Understanding Byzantine Fault Tolerance
Byzantine Fault Tolerance is a crucial concept in distributed computing, particularly in systems where components may fail or act maliciously. It ensures the system’s reliability by allowing it to function correctly even when some nodes in the network exhibit faulty behavior. This resilience is essential for systems that require high levels of trust and consistency.
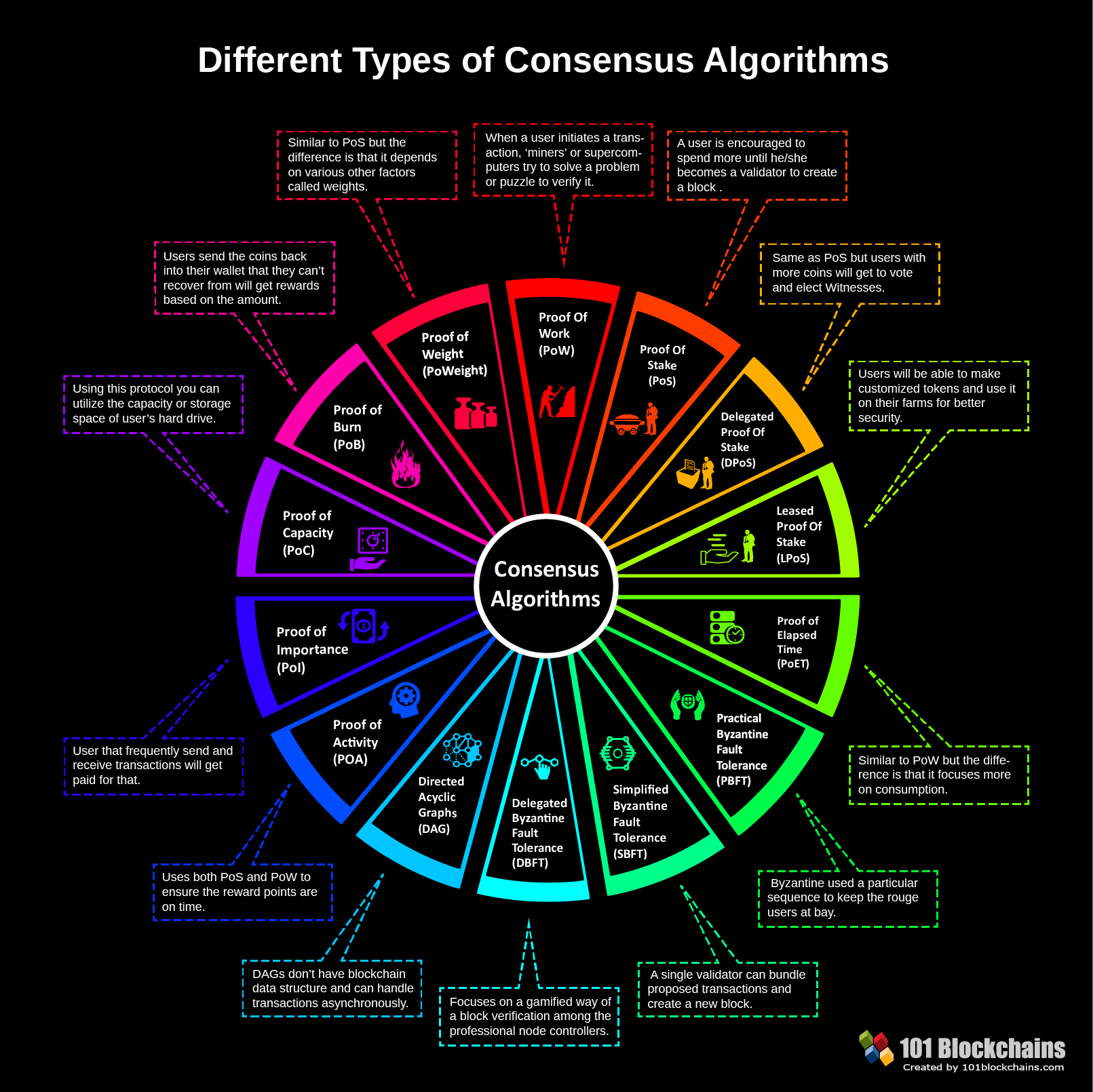
Types of Byzantine Fault Tolerance Models
Several Byzantine Fault Tolerance models exist, each with its approach to handling faulty nodes. Practical Byzantine Fault Tolerance (PBFT), HoneyBadgerBFT, and Tendermint are notable examples. PBFT, for instance, achieves consensus by having nodes exchange messages and agree on a single transaction order. Exploring these models reveals the diversity of approaches in achieving Byzantine Fault Tolerance.
Consensus Mechanisms in Byzantine Fault Tolerance
Consensus mechanisms are at the core of Byzantine Fault Tolerance models. These mechanisms ensure that all nodes in the network agree on a single state of the system, even in the presence of faulty nodes. Byzantine Fault Tolerance achieves consensus through processes like voting, verification, and multiple rounds of communication among nodes, allowing them to reach an agreement on the validity of transactions.
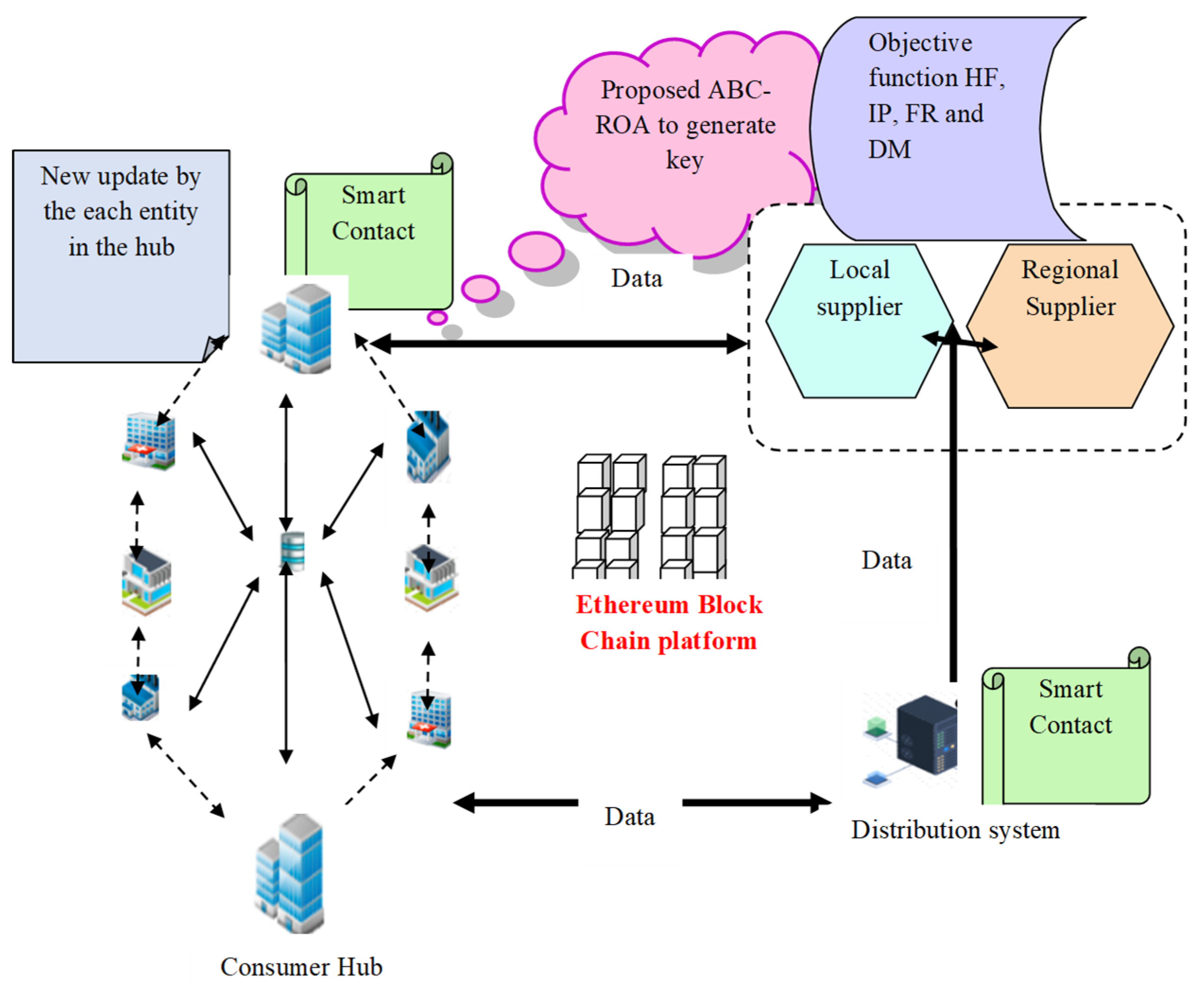
Applications in Blockchain Technology
Byzantine Fault Tolerance has found a natural home in blockchain technology. Blockchain networks, especially public decentralized ledgers, rely on consensus mechanisms to validate and agree on the order of transactions. Byzantine Fault Tolerance ensures that even in an adversarial environment, where nodes may act maliciously or fail, the blockchain can maintain its integrity and trustworthiness.
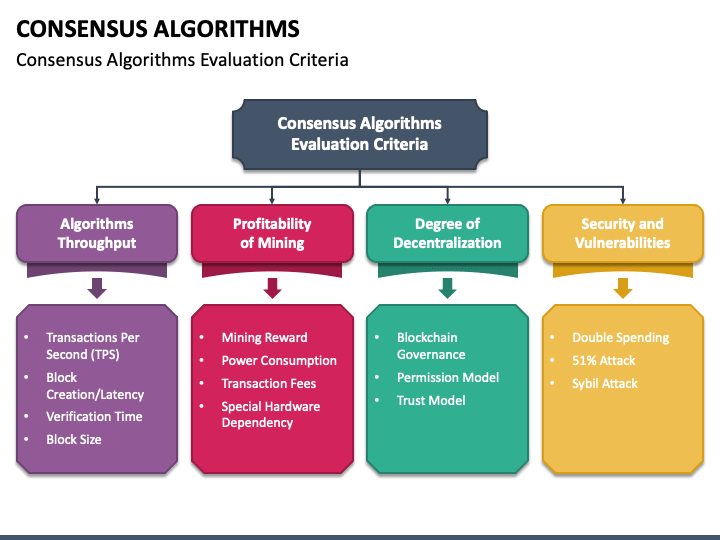
Scalability Challenges and Solutions
While Byzantine Fault Tolerance models offer robust security, scalability challenges can arise in large networks. As the number of nodes increases, the communication overhead and the number of messages exchanged can become burdensome. Addressing scalability challenges involves optimizing communication protocols, exploring parallel processing, and implementing efficient consensus algorithms.
Trade-offs in Byzantine Fault Tolerance
No system is without trade-offs, and Byzantine Fault Tolerance is no exception. Achieving high levels of fault tolerance and consensus often comes at the cost of increased communication overhead and latency. Striking the right balance between fault tolerance and system performance requires careful consideration of the specific requirements and goals of the distributed system.
Real-World Implementations and Case Studies
Byzantine Fault Tolerance models are not just theoretical concepts; they have real-world applications. From blockchain networks to distributed databases and cloud computing systems, BFT models contribute to the security and reliability of critical infrastructure. Exploring case studies provides insights into how these models perform in diverse and dynamic environments.
Innovation and Future Developments
The field of Byzantine Fault Tolerance continues to evolve, driven by ongoing research and innovations. New models and consensus mechanisms are being explored to overcome existing limitations and adapt to emerging challenges. Keeping an eye on the latest developments in BFT research is crucial for staying at the forefront of trustworthy and resilient distributed systems.
Navigating Byzantine Fault Tolerance Models – Learn More
To delve deeper into Byzantine Fault Tolerance Models, visit fireboyandwatergirlplay.com. This comprehensive resource offers additional insights, tutorials, and updates on the latest developments in the world of Byzantine Fault Tolerance and its applications.
In conclusion, Byzantine Fault Tolerance models play a vital role in ensuring the trustworthiness and resilience of distributed systems. From consensus mechanisms in blockchain to fault-tolerant databases, the principles of BFT are shaping the landscape of secure and dependable computing. Understanding and implementing these models are essential steps toward building systems that can withstand the challenges of a dynamic and sometimes adversarial environment.