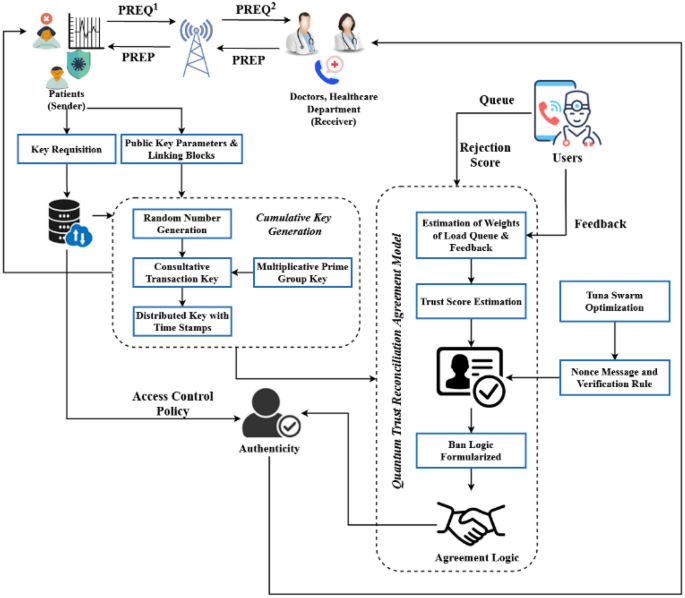
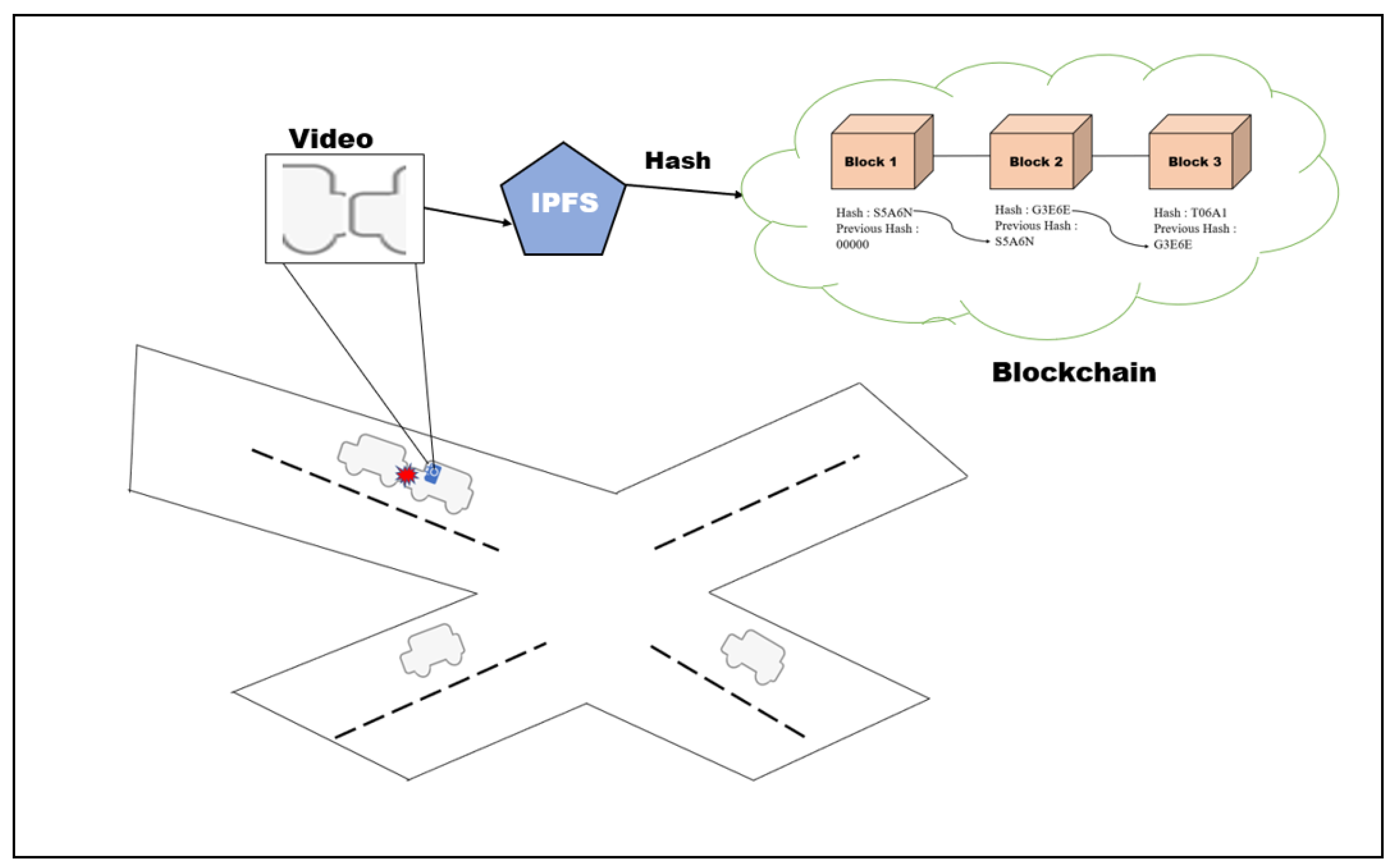
Trustless Transactions: Empowering Blockchain’s Promise
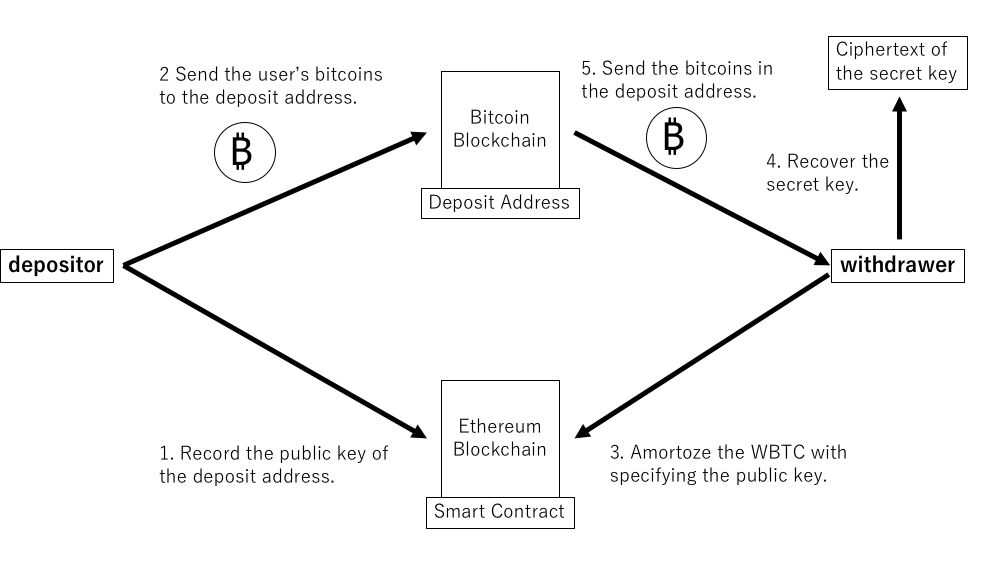
Trustless Transactions: Empowering Blockchain’s Promise
The Essence of Trustless Transactions
In the realm of blockchain technology, the concept of trustless transactions is a cornerstone. Unlike traditional systems that rely on intermediaries for trust, blockchain empowers users with the ability to transact without the need for a central authority. This paradigm shift not only enhances security but also fosters a sense of decentralization and autonomy.
Decentralization: Redefining Trust
At the heart of trustless transactions lies the principle of decentralization. Blockchain networks distribute control across a multitude of nodes, eliminating the need for a single point of trust. Every participant in the network has access to an immutable ledger, ensuring transparency and accountability. Trustless transactions become a reality when no single entity holds the power to manipulate or compromise the system.
Smart Contracts: Code as Guarantor
Smart contracts, a pivotal component of blockchain technology, contribute significantly to the trustless transaction ecosystem. These self-executing contracts automatically enforce and verify the terms of an agreement when predefined conditions are met. By eliminating the need for intermediaries, smart contracts enhance efficiency and reliability in transactions, further solidifying the trustless nature of blockchain.
Immutable Ledger: Building Trust through Transparency
Blockchain’s ledger, maintained through consensus mechanisms like Proof of Work or Proof of Stake, ensures immutability. Once a transaction is recorded, it becomes a permanent part of the chain. This unalterable history adds a layer of security, as participants can trust that the data they see is an accurate representation of the entire transaction history, making the system inherently trustless.
Security Through Cryptography
Trustless transactions are fortified by cryptographic techniques employed within blockchain networks. Public and private key pairs enable secure interactions between participants. Cryptographic hashing ensures the integrity of data, making it practically impossible for malicious actors to tamper with transaction information. These cryptographic measures form the bedrock of trustless environments within blockchain.
Trustless Transactions in Practice
To witness trustless transactions in action, one need look no further than the vast array of decentralized applications (DApps) and blockchain platforms. Whether it’s transferring digital assets, executing complex financial agreements, or participating in decentralized finance (DeFi) protocols, users can engage in trustless transactions seamlessly, thanks to the underlying principles of blockchain.
Challenges and Considerations
While the concept of trustless transactions brings numerous advantages, it is not without challenges. Scalability, regulatory concerns, and user education are factors that warrant attention. As blockchain technology continues to evolve, addressing these challenges becomes integral to realizing the full potential of trustless transactions on a global scale.
Future Horizons: Trustlessness Beyond Transactions
The evolution of trustless transactions extends beyond the scope of financial interactions. As blockchain technology matures, its applications diversify into areas such as supply chain management, voting systems, and identity verification. The trustless paradigm has the potential to redefine how we interact and transact across various aspects of our digital lives.
In the dynamic landscape of blockchain, the concept of trustless transactions stands as a testament to the transformative power of decentralized systems. Explore the possibilities and immerse yourself in the world of trustlessness. For a deeper dive into Trustless Blockchain Transactions, visit Trustless Blockchain Transactions. Discover the tools and innovations shaping the future of secure, transparent, and trustless transactions.