Exploring the Future 64-Bit Virtual Space Evolution
Exploring the Future: 64-Bit Virtual Space Evolution
Unlocking the Potential of 64-Bit Virtual Space
In the ever-expanding landscape of technology, the emergence of 64-bit virtual space marks a significant leap forward. This innovative concept not only promises to redefine digital dimensions but also holds the potential to revolutionize how we interact with virtual environments. With its advanced capabilities and immersive experiences, 64-bit virtual space opens doors to a myriad of possibilities.
Understanding the Dynamics of 64-Bit Virtual Space
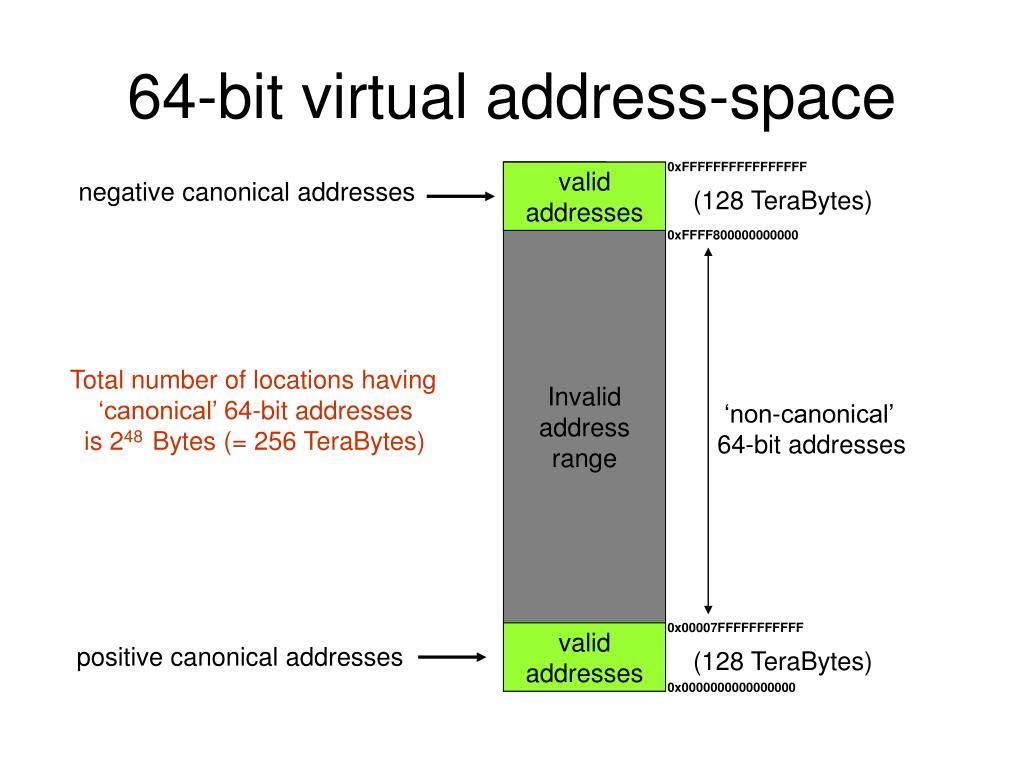
At its core, 64-bit virtual space represents a quantum leap in computational power and graphical fidelity. Unlike its predecessors, which operated within the constraints of 32-bit architecture, the transition to 64-bit brings about a paradigm shift in terms of processing capabilities and memory allocation. This newfound flexibility allows for more intricate and lifelike virtual worlds to be created, pushing the boundaries of immersion and realism.
Navigating the Features and Advantages
One of the key advantages of 64-bit virtual space lies in its ability to handle vast amounts of data with unparalleled efficiency. This means smoother gameplay, enhanced visual fidelity, and the ability to render complex environments in real-time. Furthermore, the expanded memory address space allows for larger and more detailed virtual worlds to be created, offering users a truly immersive experience like never before.
Embracing the Potential Applications
From gaming and entertainment to education and training, the potential applications of 64-bit virtual space are virtually limitless. In the gaming industry, for example, developers can create expansive open worlds with lifelike graphics and dynamic environments, providing players with a truly immersive gaming experience. Similarly, in the field of education and training, 64-bit virtual space can be used to simulate real-world scenarios, allowing users to practice and refine their skills in a safe and controlled environment.
Challenges and Considerations
While the promise of 64-bit virtual space is indeed exciting, it’s not without its challenges and considerations. One such challenge is the hardware requirements needed to fully leverage the capabilities of 64-bit architecture. This may include powerful graphics cards, ample system memory, and high-speed storage solutions, all of which can add to the overall cost of adoption. Additionally, there may be compatibility issues with older software and hardware, requiring developers to optimize their applications for 64-bit systems.
Future Prospects and Evolution
Looking ahead, the future of 64-bit virtual space is brimming with potential. As technology continues to evolve and improve, we can expect to see even greater advancements in terms of graphical fidelity, processing power, and overall immersion. This will not only benefit gamers and enthusiasts but also open up new opportunities in fields such as healthcare, architecture, and urban planning. Ultimately, 64-bit virtual space represents a bold new frontier in the realm of technology, offering endless possibilities for innovation and exploration. Read more about 64 bit virtual space


:quality(85):upscale()/2022/08/15/789/n/1922729/cf60ee3662fa8900dbdb16.27828827_.jpg)











