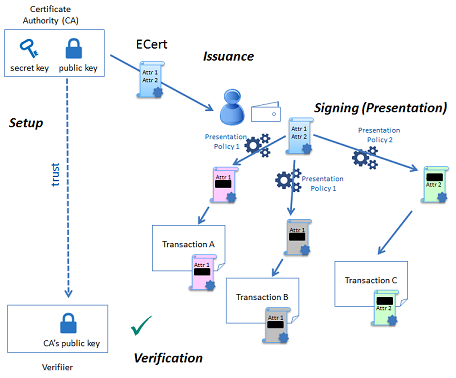
Zero-Knowledge Proofs in Action: Implementation Insights

Demystifying Zero-Knowledge Proof Implementation
Zero-Knowledge Proofs (ZKPs) have emerged as a revolutionary cryptographic tool, allowing parties to prove the authenticity of information without revealing the information itself. Understanding the implementation of Zero-Knowledge Proofs provides insights into their transformative potential across various sectors.
The Core Concept of Zero-Knowledge Proofs
At the heart of Zero-Knowledge Proofs is the ability to demonstrate knowledge of a specific piece of information without disclosing the actual content. This cryptographic concept is particularly powerful in scenarios where privacy is paramount, such as financial transactions, identity verification, and confidential data exchanges.
Protocols and Algorithms: Creating Secure Interactions
Zero-Knowledge Proof implementation relies on various protocols and algorithms. Notable among them is the zk-SNARK (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) protocol, widely used in blockchain systems. This protocol enables succinct and efficient zero-knowledge proofs, making it suitable for scenarios where computational efficiency is crucial.
Applications in Blockchain Technology
Blockchain platforms, seeking to enhance privacy without compromising transparency, have enthusiastically adopted Zero-Knowledge Proofs. ZKPs allow transactions to be validated without revealing transaction details, addressing one of the main challenges faced by public blockchains. This implementation significantly enhances the confidentiality of blockchain-based systems.
Zero-Knowledge Proofs in Cryptocurrency
In the realm of cryptocurrency, Zero-Knowledge Proofs have found applications beyond basic transactions. Privacy-focused cryptocurrencies leverage ZKPs to provide users with the ability to shield transaction amounts and participant identities. This implementation ensures a higher degree of confidentiality, aligning with the principles of financial privacy.
Challenges and Advances in Implementation
While Zero-Knowledge Proofs offer immense potential, their implementation is not without challenges. Ensuring the security and efficiency of the protocols is a constant consideration. Ongoing research and development efforts aim to address these challenges and enhance the applicability of Zero-Knowledge Proofs in real-world scenarios.
Integration with Decentralized Identity
The implementation of Zero-Knowledge Proofs intersects with the realm of decentralized identity solutions. Verifying one’s identity without disclosing unnecessary details is a crucial aspect of privacy. Zero-Knowledge Proofs play a pivotal role in decentralized identity systems, allowing users to prove specific attributes without revealing the entire dataset.
Future Outlook and Evolving Use Cases
As technology advances, the future outlook for Zero-Knowledge Proof implementation is promising. The versatility of ZKPs opens doors to evolving use cases, from secure authentication processes to confidential data sharing. The ongoing refinement of protocols and algorithms ensures that Zero-Knowledge Proofs will continue to be at the forefront of privacy-preserving technologies.
To gain a deeper understanding of Zero-Knowledge Proof implementation and its diverse applications, explore Zero-Knowledge Proof Implementation.
In conclusion, Zero-Knowledge Proofs represent a groundbreaking advancement in cryptography, offering a way to validate information without exposing sensitive details. The implementation of ZKPs in blockchain, cryptocurrency, and decentralized identity systems underscores their transformative potential. As the technology matures, Zero-Knowledge Proofs are poised to play a central role in shaping the future of privacy-preserving solutions across various domains.