Empowering Smart Contracts: Off-Chain Data Oracle Solutions
Unlocking the Potential: Off-Chain Data Oracle Solutions for Smart Contracts
In the ever-evolving landscape of blockchain technology, off-chain data oracle solutions have emerged as a vital component, enabling smart contracts to interact with real-world data seamlessly. Let’s delve into the dynamics of off-chain data oracles and their transformative impact on smart contract functionality.
Understanding Off-Chain Data Oracles: Bridging Blockchain and Real-World Data
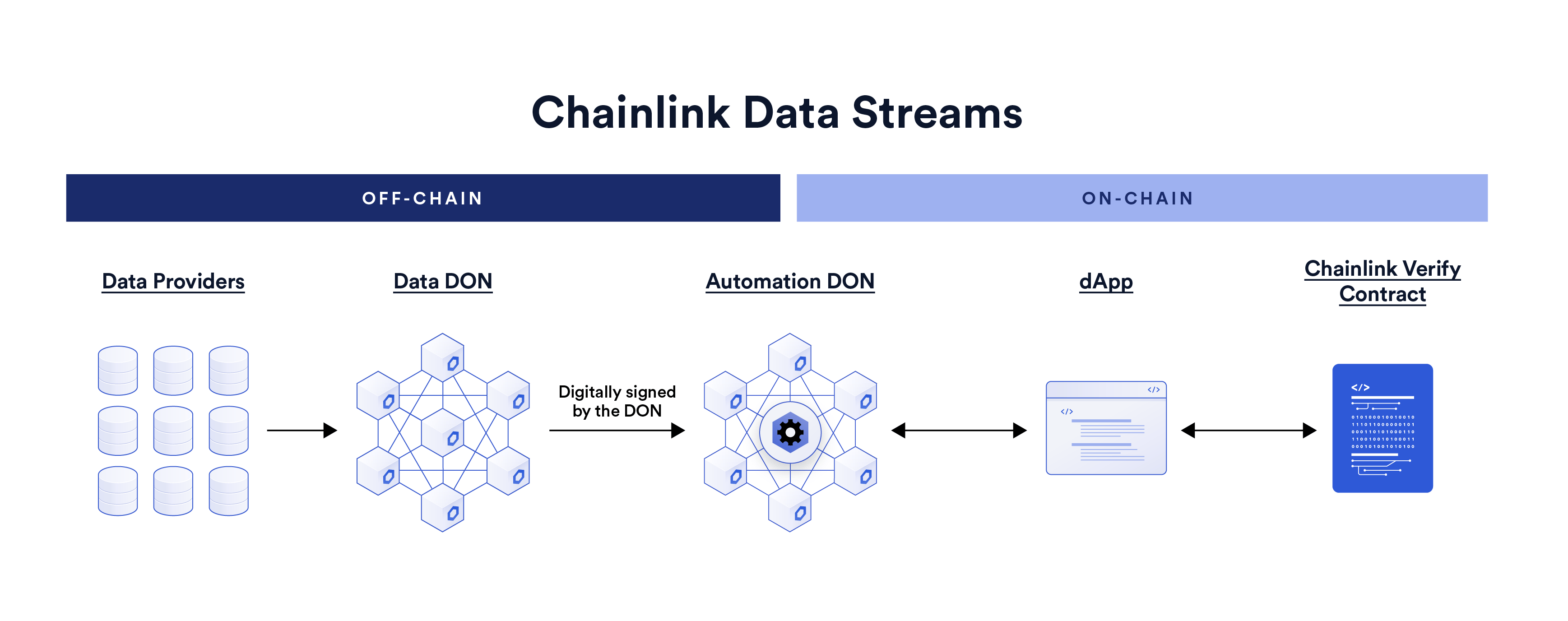
Off-chain data oracles serve as bridges between blockchain networks and external data sources. In the context of smart contracts, which operate within the constraints of on-chain data, oracles facilitate the integration of off-chain, real-world data. This functionality is crucial for smart contracts seeking to execute actions based on real-time external information.
The Limitations of On-Chain Data: Necessity of External Information
Smart contracts, by design, rely on the data available on the blockchain. However, certain use cases demand access to information beyond the blockchain’s confines. Off-chain data oracles address this limitation by providing a mechanism for smart contracts to access, verify, and execute actions based on external data without compromising the integrity of the blockchain.
Types of Off-Chain Data Oracles: Ensuring Data Reliability
Off-chain data oracles come in various types, each tailored to specific use cases and data requirements. Some oracles fetch data from centralized sources, while others aggregate information from multiple decentralized sources. Choosing the right type depends on the specific needs of the smart contract, balancing factors such as decentralization, reliability, and speed.
Decentralized Finance (DeFi) Applications: Real-Time Market Data
In the realm of decentralized finance, off-chain data oracles play a pivotal role. DeFi applications often require real-time market data for functions like price feeds, lending rates, and liquidity information. Off-chain data oracles enable smart contracts in DeFi protocols to access accurate and up-to-date information, ensuring the reliability of financial transactions.
Gaming and Sports Betting: Dynamic Event Outcomes
In gaming and sports betting applications, where smart contracts may be designed to execute based on dynamic event outcomes, off-chain data oracles become essential. These oracles provide the necessary data inputs for smart contracts to autonomously settle bets or distribute rewards based on the real-world outcomes of games and sporting events.
Weather and IoT Data Integration: Practical Use Cases
Off-chain data oracles extend their utility to practical use cases, such as weather-dependent smart contracts and Internet of Things (IoT) data integration. For example, agricultural contracts relying on weather conditions can utilize oracles to access real-time weather data, while IoT devices can contribute real-world data to smart contracts for various applications.
Ensuring Data Accuracy: Oracle Reputation and Security Measures
Maintaining the accuracy and reliability of off-chain data is paramount. Oracle reputation mechanisms, cryptographic proofs, and consensus algorithms are implemented to ensure that the data provided to smart contracts is trustworthy. Security measures are in place to mitigate the risks associated with potential oracle malfunctions or attacks.
Challenges and Solutions: Navigating the Complexity
While off-chain data oracles provide immense value, challenges exist, particularly in ensuring the security and reliability of the external data. Smart contract developers and blockchain projects are actively working on solutions, including the use of multiple oracles, reputation scoring, and decentralized consensus mechanisms to enhance the overall robustness of off-chain data integration.
The Future of Smart Contracts: A Link to Real-World Dynamics
As the adoption of blockchain technology expands, off-chain data oracles will continue to play a crucial role in the evolution of smart contracts. Their ability to bridge the gap between the digital and real-world realms unlocks new possibilities for decentralized applications, making smart contracts more versatile and applicable to a broader range of use cases.
Off-Chain Data Oracle Solutions: A Link to Innovation
In conclusion, off-chain data oracle solutions are not just tools; they represent a link to innovation in the blockchain space. By seamlessly integrating real-world data with smart contracts, these oracles pave the way for a more dynamic and practical application of blockchain technology. As blockchain ecosystems evolve, off-chain data oracles stand as a vital component, empowering smart contracts to interact with and respond to the complexities of the real world.






