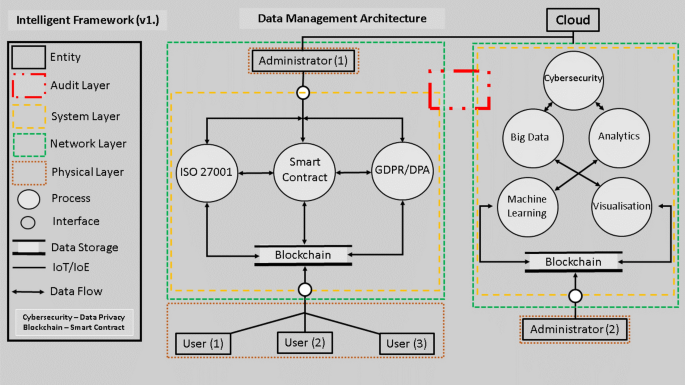
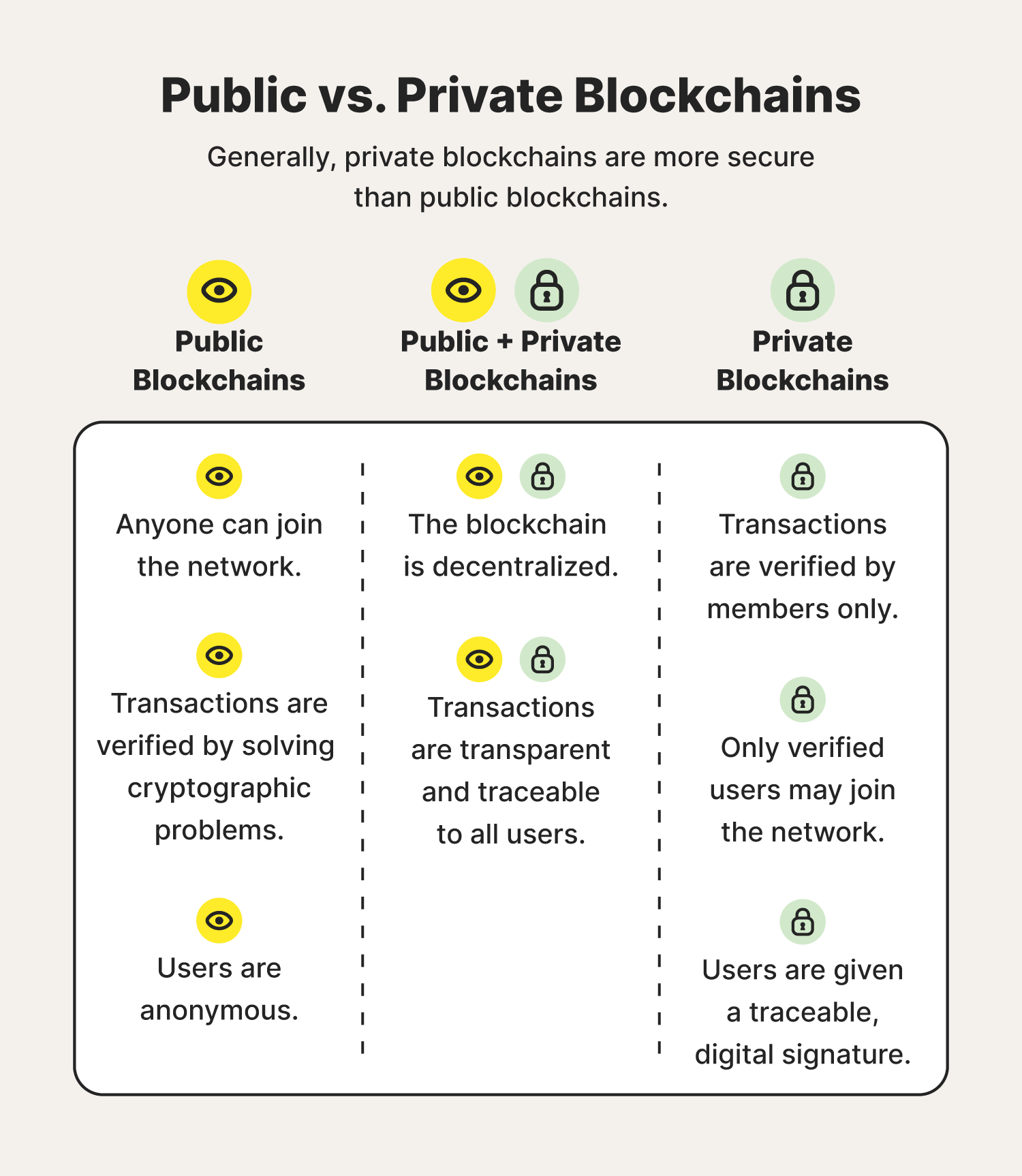
Securing Data: Privacy-Preserving Blockchain Solutions

Securing Data: Privacy-Preserving Blockchain Solutions
In the rapidly evolving landscape of blockchain technology, the need for privacy-preserving solutions has become paramount. This article explores the significance of privacy-preserving blockchain solutions, their underlying principles, and their impact on enhancing data security in decentralized systems.
The Privacy Challenge in Blockchain: Addressing Concerns
Blockchain, known for its transparency and immutability, also poses challenges related to privacy. The public nature of transactions on many blockchains can lead to concerns about sensitive data exposure. Privacy-preserving blockchain solutions aim to address these concerns by introducing mechanisms to protect the confidentiality of user data while maintaining the decentralized and trustless nature of the technology.
Zero-Knowledge Proofs: Enabling Privacy Without Disclosure
One of the key technologies empowering privacy-preserving blockchain solutions is zero-knowledge proofs. These cryptographic protocols allow a party to prove possession of certain information without revealing the information itself. By leveraging zero-knowledge proofs, blockchain transactions can be validated without disclosing the details, ensuring privacy for users while maintaining the integrity of the network.
Confidential Transactions: Concealing Transaction Amounts
Confidential transactions play a crucial role in enhancing privacy on blockchain networks. This technique involves encrypting transaction amounts, ensuring that the value transferred is visible only to the involved parties. This confidentiality layer adds an extra dimension of privacy to blockchain transactions, making it challenging for external entities to discern transaction details.
Ring Signatures and Stealth Addresses: Masking Identities
Privacy-preserving blockchain solutions often incorporate cryptographic techniques such as ring signatures and stealth addresses. Ring signatures enable a user to sign a transaction on behalf of a group, making it impossible to determine which specific member initiated the transaction. Stealth addresses add another layer by concealing the recipient’s identity, enhancing the overall privacy of blockchain transactions.
Homomorphic Encryption: Performing Operations on Encrypted Data
Homomorphic encryption is a powerful tool in the privacy-preserving toolkit, allowing computations to be performed on encrypted data without decrypting it. In the context of blockchain, this means that smart contracts can operate on encrypted inputs, preserving the confidentiality of sensitive information while still executing complex operations. Homomorphic encryption contributes significantly to privacy-focused blockchain solutions.
Decentralized Identity Solutions: Empowering Users
Ensuring privacy goes beyond transactional data. Decentralized identity solutions enable users to maintain control over their personal information. By leveraging self-sovereign identity principles, users can selectively disclose information without compromising their entire identity. This approach empowers individuals to participate in blockchain networks while retaining control over their private data.
Privacy Coins: Tailoring Solutions for Confidentiality
Privacy coins, designed with a primary focus on confidentiality, play a pivotal role in the privacy-preserving blockchain ecosystem. Cryptocurrencies like Monero and Zcash integrate advanced privacy features, including confidential transactions and zero-knowledge proofs, providing users with enhanced privacy options for their financial transactions.
Regulatory Challenges: Balancing Privacy and Compliance
While privacy-preserving blockchain solutions offer significant advantages, they also raise regulatory challenges. Striking a balance between privacy and compliance with regulations, particularly in financial transactions, remains a complex task. Solutions that enable regulatory compliance without compromising user privacy are essential for the widespread adoption of privacy-preserving blockchain technologies.
The Road Ahead: Integration and Awareness
Looking ahead, the successful integration of privacy-preserving blockchain solutions into mainstream applications is contingent on raising awareness and fostering collaboration. Developers, businesses, and regulatory bodies must work together to navigate the complexities of privacy in blockchain technology. Education and advocacy will play crucial roles in driving the adoption of these solutions.
Conclusion: Privacy as a Fundamental Right
In conclusion, privacy-preserving blockchain solutions represent a significant step forward in addressing the privacy challenges inherent in decentralized systems. As blockchain technology continues to mature, prioritizing privacy as a fundamental right becomes imperative. The integration of advanced cryptographic techniques, decentralized identity solutions, and privacy coins collectively contributes to a more secure and private blockchain ecosystem.
Explore more about Privacy-Preserving Blockchain Solutions here.