Interplanetary File System (IPFS): Decentralized Data Sharing
Navigating the Cosmos: Introduction to Interplanetary File System (IPFS)
In the vast universe of data sharing and storage, the Interplanetary File System (IPFS) emerges as a decentralized and revolutionary solution. This article embarks on a journey to unravel the intricacies of IPFS, exploring its foundations, key features, and the transformative impact it has on the way we share and access information.
Breaking the Traditional Mold: The Concept of Decentralization in IPFS
Unlike traditional file systems that rely on central servers, IPFS introduces a decentralized approach to data storage and sharing. The core concept revolves around creating a peer-to-peer network where each user, or node, becomes a part of the shared file system. This departure from centralization enhances data resilience, fosters redundancy, and contributes to a more efficient and fault-tolerant system.
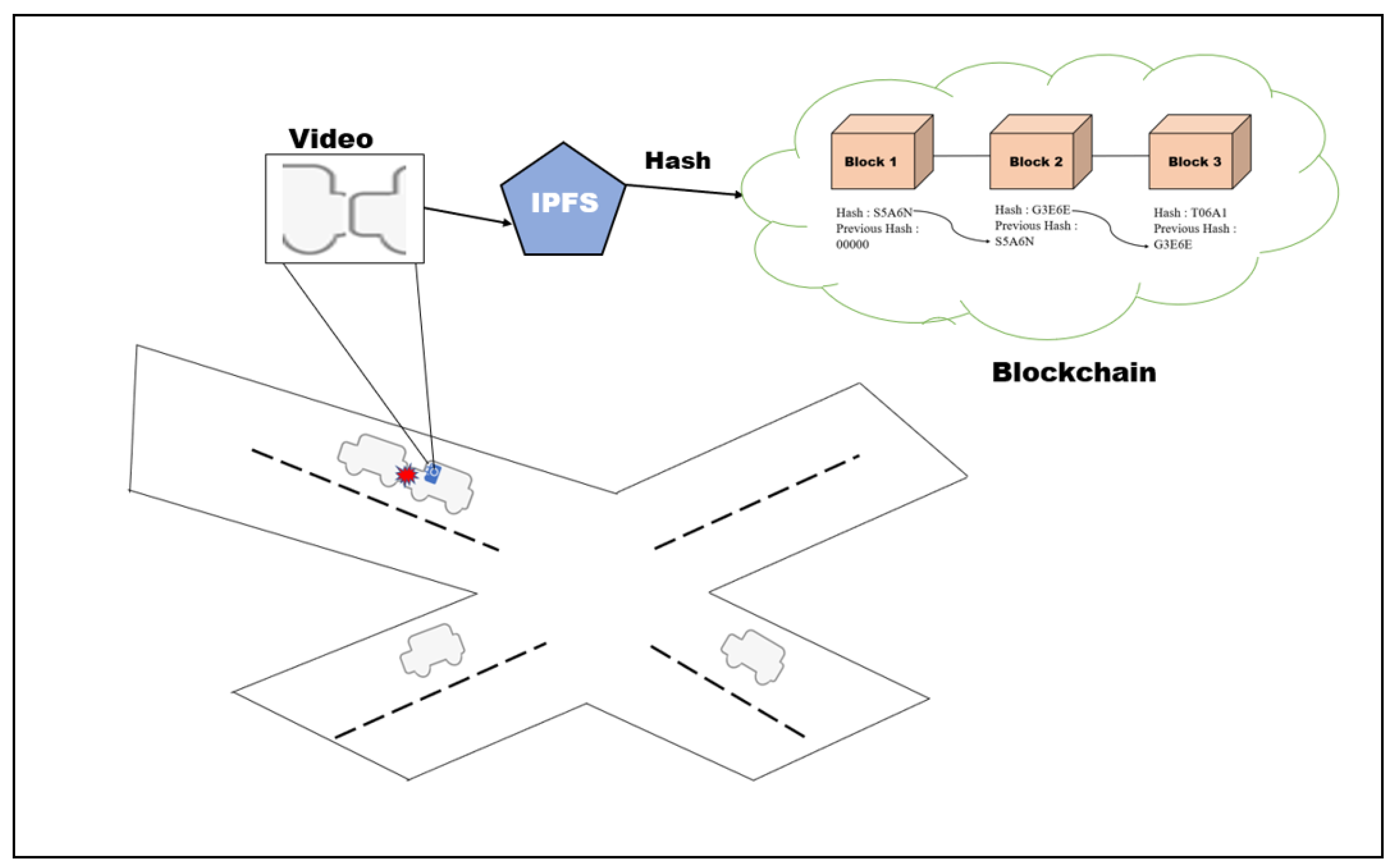
MerkleDag and Content Addressing: Redefining File Identification
At the heart of IPFS lies the MerkleDag data structure, which enables content addressing. In traditional systems, files are identified by their location, but in IPFS, content is identified by its hash. This content addressing mechanism ensures that the data’s integrity is preserved, as any modification to the content results in a different hash. This unique approach eliminates redundancy and enhances data verifiability.
Distributed Hash Tables (DHT): Navigating the Web of Data
IPFS utilizes Distributed Hash Tables (DHT) to enable efficient content discovery within the network. DHT distributes the responsibility of maintaining the network’s address space across participating nodes, enabling seamless and decentralized lookups. This mechanism ensures that users can efficiently locate and retrieve content, regardless of its physical location within the IPFS network.
Offline Access and Resilience: Overcoming Connectivity Challenges
One of IPFS’s notable features is its ability to provide offline access to content. By storing requested data locally, nodes can access and share content even when disconnected from the broader network. This offline resilience addresses connectivity challenges and makes IPFS a suitable solution for scenarios with intermittent or limited internet access.
IPFS in Action: Use Cases Across Industries
The versatility of IPFS extends across various industries, showcasing its potential for transformative applications. From decentralized web hosting and file sharing to content distribution and archival, IPFS’s decentralized nature makes it adaptable to diverse use cases. Its resilience, coupled with efficient data retrieval, positions IPFS as a viable solution for industries seeking a decentralized and robust file-sharing infrastructure.
IPFS and Web3: Synergies for a Decentralized Internet
As the world transitions towards Web3, characterized by decentralized applications and services, IPFS emerges as a crucial component in this paradigm shift. IPFS provides the decentralized storage and retrieval infrastructure needed for the distributed and peer-to-peer nature of Web3 applications, aligning with the principles of a more open, equitable, and user-centric internet.
Gateway Services: Bridging IPFS with Traditional Web Browsers
To facilitate widespread adoption, IPFS leverages gateway services that bridge the decentralized IPFS network with traditional web browsers. These gateways act as intermediaries, allowing users to access IPFS content through conventional browsers. This integration enhances the accessibility of IPFS content, making it more user-friendly and encouraging broader adoption.
Challenges and Considerations: Navigating the Cosmos of IPFS
While IPFS brings significant advantages, it is not without challenges. Issues such as slow content retrieval, reliance on gateway services, and the need for wider adoption present considerations for users and developers. However, ongoing development and community efforts aim to address these challenges, ensuring the continuous improvement and maturation of the IPFS ecosystem.
Exploring the Cosmos: Dive into Interplanetary File System (IPFS)
For those curious to explore the vast cosmos of IPFS, an interactive experience awaits. Interplanetary File System (IPFS) provides a gateway to understanding and engaging with the decentralized world of data sharing. This link invites exploration into the practical applications and implications of IPFS, offering a firsthand experience of its transformative potential.
Conclusion: Navigating the Future with Interplanetary File System (IPFS)
In conclusion, Interplanetary File System (IPFS) represents a paradigm shift in how we approach data sharing and storage. Its decentralized architecture, content addressing, and resilience make it a compelling solution for the challenges of the modern internet. As we navigate the cosmos of information, IPFS stands as a guiding star, pointing towards a decentralized, efficient, and user-centric future for data sharing and storage.


.gif) “The Edge of Reason” by Melissa Snodgrass is a story of good versus evil, of science versus superstition. It entertains while skillfully raising questions about the origins of religion and technology.
“The Edge of Reason” by Melissa Snodgrass is a story of good versus evil, of science versus superstition. It entertains while skillfully raising questions about the origins of religion and technology..jpg) Last year we were discussing the challenges of selling Taiwan our latest weapon systems in case they wanted to defend themselves against a Chinese forced reunification. If we don’t there would be little reason for China not to force their political will, but if we do, it’s well known that Chinese spies have infiltrated the Taiwan Military and political leadership, and thus, might someday use that same technology against us, our allies, or sell it to our enemies. Okay so, let’s talk.
Last year we were discussing the challenges of selling Taiwan our latest weapon systems in case they wanted to defend themselves against a Chinese forced reunification. If we don’t there would be little reason for China not to force their political will, but if we do, it’s well known that Chinese spies have infiltrated the Taiwan Military and political leadership, and thus, might someday use that same technology against us, our allies, or sell it to our enemies. Okay so, let’s talk. Like all fads that were once hot, is quickly becoming supplanted by a comer, . It was just a few short years ago, that everyone who was online had a MySpace page, now it’s Facebook’s turn.
Like all fads that were once hot, is quickly becoming supplanted by a comer, . It was just a few short years ago, that everyone who was online had a MySpace page, now it’s Facebook’s turn. If you thought that you are not technically equipped to run your PC, you can now groom yourself for that. You can make a meaningful start by visiting online information technology forums. Visiting such online computer forums which are free and available to you 24 hours a day, 7 days a week, and 365 days a year can be your own technical university classroom to upgrade your PC learning skills that will match your own technical needs for your own PC use.
If you thought that you are not technically equipped to run your PC, you can now groom yourself for that. You can make a meaningful start by visiting online information technology forums. Visiting such online computer forums which are free and available to you 24 hours a day, 7 days a week, and 365 days a year can be your own technical university classroom to upgrade your PC learning skills that will match your own technical needs for your own PC use. There is no written evidence which can tell us exactly who has coined the phrase educational technology. Different educationists, scientists and philosophers at different time intervals have put forwarded different definitions of Educational Technology. Educational technology is a multifaceted and integrated process involving people, procedure, ideas, devices, and organization, where technology from different fields of science is borrowed as per the need and requirement of education for implementing, evaluating, and managing solutions to those problems involved in all aspects of human learning.
There is no written evidence which can tell us exactly who has coined the phrase educational technology. Different educationists, scientists and philosophers at different time intervals have put forwarded different definitions of Educational Technology. Educational technology is a multifaceted and integrated process involving people, procedure, ideas, devices, and organization, where technology from different fields of science is borrowed as per the need and requirement of education for implementing, evaluating, and managing solutions to those problems involved in all aspects of human learning. The term green technology may conjure images of scientists designing futuristic solar or wind energy equipment. But it is more than that.
The term green technology may conjure images of scientists designing futuristic solar or wind energy equipment. But it is more than that. Ray Bradbury’s The Veldt and the article Modern Technology Is Changing the Way our Brains Work, Says Neuroscientist by Susan Greenfield each reveal the change in young folks’s lives by limitless access to quite a lot of current know-how of their each day lives. Those of us who remember the Nineteen Eighties, when computers have been first making their method into our school rooms, probably additionally bear in mind a substantial amount of bad software program. Spy Net’s infrared night imaginative and prescient binoculars use actual IR night time imaginative and prescient technology that will help you see things as much as 50 feet away in total darkness. I would assume that there has to be a new technology the place roadsigns transmit info through radio signals, or possibly Wi-Fi.
Ray Bradbury’s The Veldt and the article Modern Technology Is Changing the Way our Brains Work, Says Neuroscientist by Susan Greenfield each reveal the change in young folks’s lives by limitless access to quite a lot of current know-how of their each day lives. Those of us who remember the Nineteen Eighties, when computers have been first making their method into our school rooms, probably additionally bear in mind a substantial amount of bad software program. Spy Net’s infrared night imaginative and prescient binoculars use actual IR night time imaginative and prescient technology that will help you see things as much as 50 feet away in total darkness. I would assume that there has to be a new technology the place roadsigns transmit info through radio signals, or possibly Wi-Fi.






