Argo Coin Pioneering the Next Generation of Currency
Unlocking the Potential of Argo Coin
Introduction
Argo Coin has been making waves in the world of cryptocurrency, offering investors a promising opportunity to participate in the digital finance revolution. With its innovative approach and forward-thinking technology, Argo Coin is quickly gaining traction as a viable investment option in today’s ever-evolving market landscape.
Understanding Argo Coin
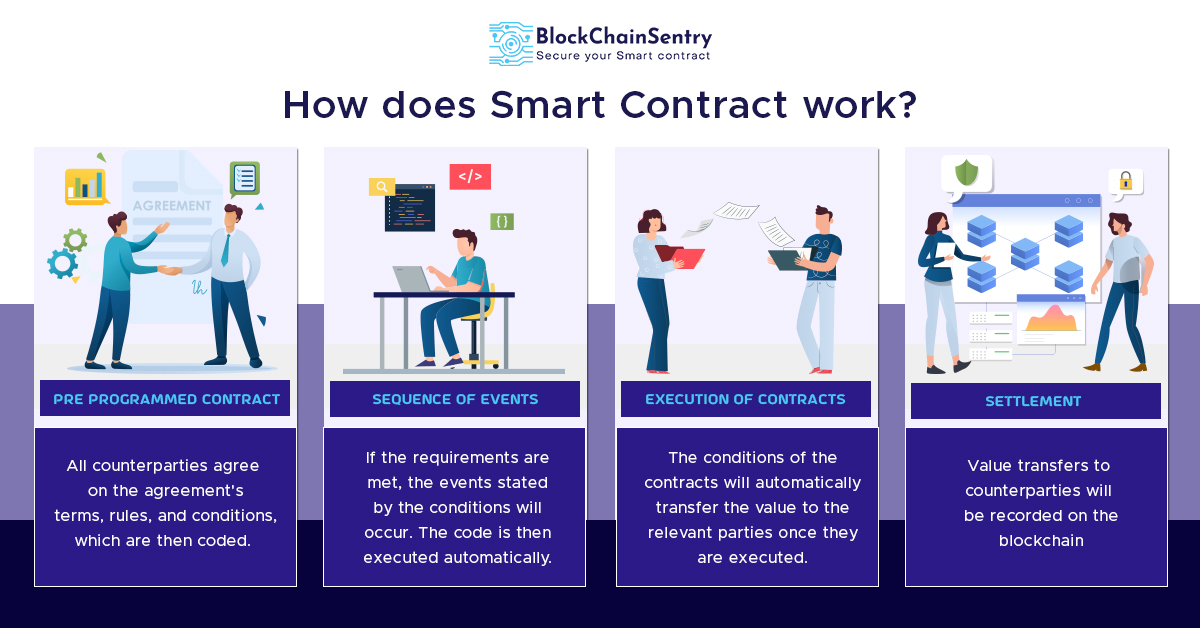
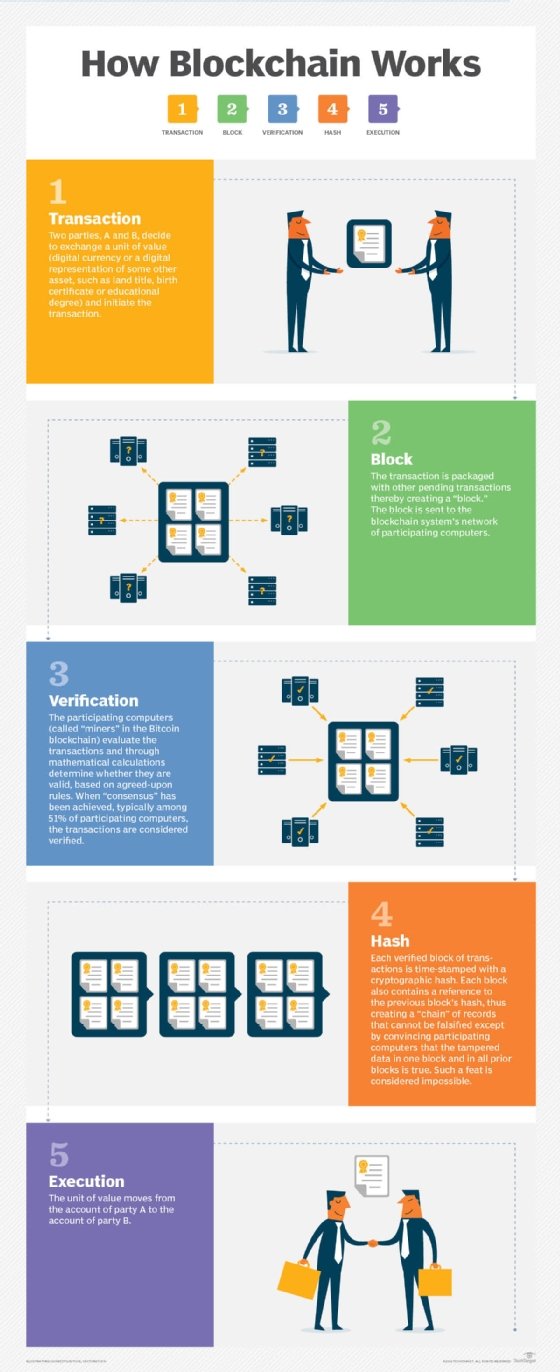
At its core, Argo Coin is a decentralized digital currency built on blockchain technology. This means that transactions involving Argo Coin are secure, transparent, and immutable, providing users with a level of trust and reliability that is often lacking in traditional financial systems.
The Technology Behind Argo Coin
Argo Coin utilizes advanced cryptographic techniques to secure its network and validate transactions. This ensures that each transaction is legitimate and cannot be tampered with, providing users with peace of mind knowing that their funds are safe and secure.
The Benefits of Argo Coin
One of the main advantages of Argo Coin is its low transaction fees and fast processing times. Unlike traditional banking systems that may take days to process transactions, Argo Coin transactions are typically processed within minutes, allowing users to send and receive funds quickly and efficiently.
Investing in Argo Coin
For investors looking to diversify their portfolio, Argo Coin offers a unique opportunity to participate in the growing cryptocurrency market. With its strong technological foundation and dedicated development team, Argo Coin has the potential to become a major player in the digital finance space in the coming years.
The Future of Argo Coin
As the digital finance revolution continues to unfold, Argo Coin is poised to play a significant role in shaping the future of money. With its innovative technology and forward-thinking approach, Argo Coin has the potential to revolutionize the way we think about finance and empower individuals around the world to take control of their financial destinies.
Risks and Challenges
While Argo Coin holds great promise, it is not without its risks and challenges. Like any investment, investing in Argo Coin carries inherent risks, including volatility and regulatory uncertainty. It is important for investors to carefully consider these risks before making any investment decisions.
The Importance of Due Diligence
Before investing in Argo Coin or any other cryptocurrency, it is crucial for investors to conduct thorough due diligence and research. This includes understanding the technology behind the coin, evaluating its market potential, and assessing the credibility of the development team behind it.
Conclusion
In conclusion, Argo Coin represents an exciting opportunity for investors looking to participate in the digital finance revolution. With its innovative technology, low transaction fees, and fast processing times, Argo Coin has the potential to become a major player in the cryptocurrency market in the years to come. However, it is important for investors to carefully consider the risks and challenges associated with investing in Argo Coin and to conduct thorough due diligence before making any investment decisions. Read more about argo coin